Reporters/Yu-Chi Su, Alsina Betha, Mohammad Fahmirullah, Chin-Ying Tsai
Technologies and digital culture streams have become an integral part of people’s life in Taiwan since many cannot live without them. Beneath our streets and above our heads, users of technologies have braided every signal into the Internet through the satellites. Every day, users get almost everything uploaded, including social media information, email messages, or even passwords of bank accounts.
However, some people with malicious intent may hack into the system, sabotage other people’s data with great finesse, and worst of all, steal confidential documents. Therefore, awareness in protecting one’s data is much needed especially in this “smart era.” In other words, cybersecurity has become a necessity to protect systems, networks, and programs from digital attacks.

Perspicacious Undercover Hacker Figures
Although the Internet may seem safe, one must be cautious since there are always threats and scams. Behind the networking system, there is an invisible figure called “man in the middle” who knows all the users’ information. Despite being the so-called “man in the middle,” he is also tagged as a hacker. There are in fact two kinds of hackers: white hat hacker and black hat hacker.
An ethical hacker, known as the white hat hacker, is a security hacker who can gain access to the systems with the intention of fixing the identified weaknesses. This kind of hacker may also perform penetration testing and vulnerability assessments. While “cracker” is the opposite of the white hat, and is known as the black hat hacker who gets unauthorized access to computer systems for personal gain.
Joe, a cybersecurity consultant in Taiwan, explained, “In general, most hackers’ goal is to find out the first hand vulnerability, also called the zero-day vulnerability, and become famous.” He added, “For the white hat hackers, they would normally start profiling forms to submit to Common Vulnerabilities and Exposures (CVEs), which fortunately, Taiwan has an organization (TWCERT/CC) that is in charge of doing so.”
According to the National Institute of Standards and Technology (NIST), the definition of vulnerability is “weakness in an information system, system security procedures, internal controls, or implementation that could be exploited or triggered by a threat source.” The intent of the hackers is usually to steal corporate data, violate privacy rights, transfer funds from bank accounts, and so forth.
Hackers are not always related to the coding system but could also be associated with the application tools that existed before. When it comes to skill level, Script Kiddies usually use automated tools that are not written by themselves to spread the viruses. Unlike Script Kiddies, Hacktivists are groups of criminals who unite together to carry out cyber-attacks that they feel do not align with their political practices. Two of the most common ways they attack their targets are by stealing sensitive information and exposing it or denying service where a server is overloaded until it finally crashes.
Generally, there are two teams in cybersecurity: the red team and the blue team. The red team is for the attackers, while the blue team is for the defenders. When the red team has succeeded in breaking into the security system, it is the blue team’s duty to strengthen the security system and find out the cause behind the failure of the security system.
The stages of hackers performing the task of hacking are mostly for information gathering and exploiting. After successfully gaining access to the escalation privilege, hackers will put a backdoor to maintain access and cover the track by clearing all log files. At the same time, the most widely used and possible combination of hacking methods is an injection, some brute force login passwords, and sensitive information disclosure. So, it is fair to say that no matter how strong the safety system protection could be, there is always a gap to break into it.

Hackers’ Scandalous Crimes
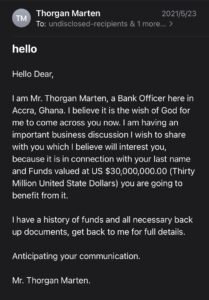
Cybersecurity vulnerabilities are usually made by people out of negligence and some ill-intent software engineerswho are tempted to commit cybersecurity crime; however, Joe stressed that no criminal activities can be tolerated. The most common form of the attack comes in the form of an email mimicking the identity of one of the company’s vendors or someone who has a lot of authority in the company. The fundamental goal of this strategy is to exploit an organization’s employees to bypass one or more security layers, which aims to access data that are confidential.
Xie Jia-xing, leader of the Infrastructure Division in the Department of Information Technology of Taipei City Government, pointed out, “Being the capital of Taiwan, Taipei City Government has always been the favorite target for the black hat hackers simply because its citizens’ personal information is so valuable.”
During mid-March 2018, news broke out about how Cambridge Analytica, a London-based data-mining firm with ties to the U.S. President Donald Trump, lifted Facebook profiles of tens of millions of users without their permission in an attempt to sway elections. It is utterly proven that everything on the Internet will not be completely safe.
Talking about the biggest crisis of information security in Taiwan, Xie emphasized that black hat hackers have organized themselves into a “real company” just like white hat hackers. Because of their cunning tactics, it is difficult to uncover their attacks. Alexander Michael of the Security Engineer Intern said, “Many hackers pretend to work in companies with ulterior motives. They even disguise themselves as cybersecurity personnel, but actually, they are whistleblowers who are capable of leaking data to the outside world.”
As for cybersecurity crimes, one can find phishing attacks, privacy violations, electronic funds transfers, denial of service attacks, and so on. According to Security Magazine, in 2020, almost a third of the breaches incorporated social engineering techniques, of which 90% were phishing. Social engineering attacks include, but are not limited to phishing emails, scareware, quid pro quo, and other techniques, all of which tend to manipulate human psychology to attain specific goals.

Michael further pointed out, “The manipulation of human psychology is linked to social engineering since a broad range of malicious activities are accomplished through human interactions either indirectly or directly.” He added, “In some cases, the perpetrator claiming to be a bank employee would ask for the user’s account number, saying that the bank account number has been blocked. The victim might panic and even unconsciously tell the perpetrator the account number.” Therefore, it is obvious that cybersecurity is not only focused on network or application security, but could also be related to people’s psychological states.
Notorious Perspective of Hackers
Hackers are stereotypically referred to as illegal, network evil, and socially weird cyber-criminals. Even though this might be true, not all modern-day hackers are criminals. On the contrary, many hackers use their knowledge for a good cause. Some of the hackers even work for big companies to protect their data system, seeking the bug system’s weakness.
Schumacher Goldwin, a Cyber Security student from Bina Nusantara University, said, “Hacker is just like a knife. It can help someone in cooking and can be used to kill someone or something. If hackers are working for us, there is nothing to worry about, but it will be very destructive if they are against us.” He reiterated, “Mostly, hackers pretend to work anonymously or work as heroes without the cape. Some of them also contribute to the country and cooperate with the government to protect the country’s important data from being tapped and spied upon by other countries.”
Intelligence technology era has developed rapidly in modern times and will always be upgraded any time. Cybersecurity must be updated or it might be left behind. In Michael’s opinion, in the future, Industry 5.0 cybersecurity will be in great demand. The difference between Industry 4.0 and 5.0 lies in the fact that Industry 4.0 evaluates the quantity and mass production, while Industry 5.0 evaluates life standard, creativity, and high-quality custom-made products.
With regards to the personal data protection act, Joe gave his advice on password safety by saying, “No matter what the things that have been asked to do by someone, never ever show your password to anyone. Also the longer password, the more difficult it will be hacked. The best way to maintain password security is to use a password manager that is only needed for you to have remembered once, and then it will do the rest for you.”
Photo/Mohammad Fahmirullah
Moreover, people should always be aware of illegal apps because hackers can slip something into the apps, spread viruses, steal the data, and even do the monitoring. Goldwin cautioned, “Never reveal your sensitive data such as credit card numbers or passwords to a third-party website that you do not trust.”
Since our society is more technologically reliant than ever, the importance of cybersecurity is on the rise. Moreover, people should not only focus on the negative impact caused by the hackers but should also look at what the hackers have contributed. The fact is straight-out, with the existence of black hats behind the cyber world, there will be the need for white hats which come up with inventions in the IT industry to upgrade it to the newest system. It can be said that the roles of cybersecurity as attacker and defender will always coexist as IT develops. Still, the networking users must always remain vigilant in any situation. Eventually, users are the weakest with the biggest vulnerability; therefore, people should always have cybersecurity awareness and pay more attention to every link before clicking, in order to protect their data from theft and damage.

